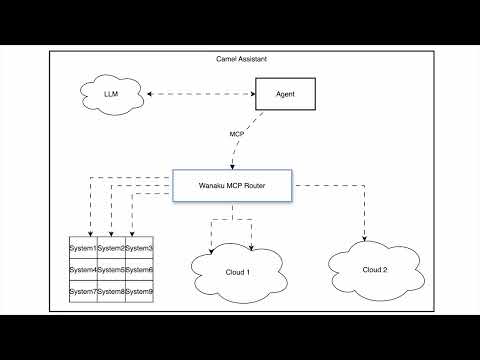
I published a walk-through video about building an AI Agent using #ApacheCamel, #LangFlow and the Wanaku #MCP Router
#langflow
Recent Langflow Vulnerability Exploited by Flodrix Botnet https://www.securityweek.com/recent-langflow-vulnerability-exploited-by-flodrix-botnet/ #Malware&Threats #exploited #Langflow #botnet #AI
Recent Langflow Vulnerability Exploited by Flodrix Botnet https://www.securityweek.com/recent-langflow-vulnerability-exploited-by-flodrix-botnet/ #Malware&Threats #exploited #Langflow #botnet #AI
LangWHAT?
You've seen names like LangChain, LangGraph, LangFlow or LangSmith – but what’s really behind them?
 LangChain helps us build LLM apps via modular code.
LangChain helps us build LLM apps via modular code.
 LangGraph adds branching logic and multi-agent workflows.
LangGraph adds branching logic and multi-agent workflows.
 LangFlow lets us create flows with drag & drop.
LangFlow lets us create flows with drag & drop.
 LangSmith monitors and evaluates our LLM stack.
LangSmith monitors and evaluates our LLM stack.
LangChain, LangGraph and LangSmith come from the same ecosystem. LangFlow is a visual builder developed independently by DataStax.
Tried both LangChain and Langflow to build the same chatbot — Medium article coming shortly.
Confused between LangGraph and LangFlow?
LangGraph is a code-first framework from the LangChain team. Perfect for building stateful, multi-agent, complex LLM workflows with branching, loops, and control logic.
LangFlow is a visual builder made by a third party. Great for drag-and-drop prototyping of LangChain apps—no deep coding needed.
Use LangGraph for logic-heavy orchestration.
Use LangFlow to experiment and visualize quickly.
CVE-2025-3248: Renewed Interest in Langflow Remote Code Execution
About the exploit:
#Langflow is a widely used #opensource library for building AI agents, backed by corporate support from #Datastax (now #IBM). The tool provides a web-based, drag-and-drop interface for creating agentic workflows, making it particularly attractive to businesses, but also a high-value target for exploits. Given that such workflows often integrate with critical business databases and tools, security vulnerabilities in Langflow could have severe consequences.
This risk is not hypothetical. Langchain, another leading AI framework, has already been associated with over 30 CVEs, underscoring the security challenges in the fast-moving LLM development ecosystem.
The vulnerability in Langflow allowed unauthenticated attackers to execute arbitrary code on the host machine. Discovered and disclosed by Horizon3 in late February, the issue was patched in version 1.3, released at the end of March. Below is a detailed timeline of the discovery and remediation process.
Trend analysis:
Feb 25, 2025: The vulnerability is disclosed to DataStax by Horizon3.
Mar 5, 2025: DataStax fixes the vulnerability in the development branch.
Mar 31, 2025: Langflow 1.3.0 releases, containing a fix for CVE-2025-3248.
April 7, 2025: CVE-2025-3248 is published to the NVD.
April 9, 2025: The exploit is leaked to the public, and the CrowdSec Network starts tracking the exploit.
April 11-12, 2025: The CrowdSec Network observes a first wave of exploitation attempts by approximately 200 machines.
April 12 - May 14, 2025: Attackers disappear, with barely any attacks registered in the CrowdSec Network.
May 14 - 23, 2025: The CrowdSec Network observes a renewed, smaller wave of attacks, peaking out at around 100 involved machines.
How to protect your systems:
Patch: If you haven’t already, ensure your publicly exposed Langflow instance is updated with the latest patch.
Preemptive blocking: Use Crowdsec CTI to block IPs exploiting CVE-2025-3248
https://app.crowdsec.net/cti?q=cves%3ACVE-2025-3248
Stay proactive: Install the Crowdsec Web Application Firewall to stay ahead of exploit attempts with 100+ virtual patching rules available
https://app.crowdsec.net/cti?q=cves%3ACVE-2025-3248
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and #collaborative #cybersecurity http://crowdsec.net/
Jetzt patchen! Warnung vor Schadcode-Attacken auf #FreeType und #Langflow | Security https://www.heise.de/news/Jetzt-patchen-Warnung-vor-Schadecode-Attacken-auf-FreeType-und-Langflow-10374264.html #Patchday
Critical Langflow Vulnerability (CVE-2025-3248) Actively Exploited, Warns CISA https://hackread.com/langflow-vulnerability-cve-2025-3248-actively-exploited-cisa/ #ArtificialIntelligence #Cybersecurity #Vulnerability #AgenticAI #Security #Langflow #security #AI
Critical Langflow Vulnerability (CVE-2025-3248) Actively Exploited, Warns CISA – Source:hackread.com https://ciso2ciso.com/critical-langflow-vulnerability-cve-2025-3248-actively-exploited-warns-cisa-sourcehackread-com/ #1CyberSecurityNewsPost #artificialintelligence #CyberSecurityNews #cybersecurity #Vulnerability #AgenticAI #Hackread #Langflow #security #AI
#CISA warns CVE-2025-3248 in Langflow is being actively exploited. Critical RCE flaw allows full server takeover. Patch to v1.3.0 ASAP.
#Infosec #CVE2025 #Langflow #CyberSecurity
Read: https://hackread.com/langflow-vulnerability-cve-2025-3248-actively-exploited-cisa/
'Easily Exploitable' #Langflow #Vulnerability Requires Immediate Patching. The vulnerability, which has a CVSS score of 9.8, is under attack and allows threat actors to remotely execute arbitrary commands on servers running the agentic #AI builder.
https://www.darkreading.com/vulnerabilities-threats/easily-exploitable-langflow-vulnerability-patching
#security
U.S. #CISA adds #Langflow flaw to its Known Exploited Vulnerabilities catalog
https://securityaffairs.com/177481/hacking/u-s-cisa-adds-langflow-flaw-to-its-known-exploited-vulnerabilities-catalog.html
#securityaffairs #hacking
Critical Vulnerability in AI Builder Langflow Under Attack https://www.securityweek.com/critical-vulnerability-in-ai-builder-langflow-under-attack/ #ArtificialIntelligence #vulnerability #exploited #Langflow #CISAKEV #AI
Critical Vulnerability in AI Builder Langflow Under Attack https://www.securityweek.com/critical-vulnerability-in-ai-builder-langflow-under-attack/ #ArtificialIntelligence #vulnerability #exploited #Langflow #CISAKEV #AI
Сравнение low-code редакторов для разработки приложений на основе LLM
Привет, Habr! Наша команда LLM-разработки подготовила статью с анализом low-code редакторов для разработки пайплайнов на базе LLM-моделей. Тема сравнения редакторов назревала давно, так как мы активно используем данные инструменты в своей работе и зачастую сталкиваемся с различными ограничениями решений. Данная статья будет полезна командам, которые только выбирают среду разработки пайплайнов для своих LLM-приложений и ИИ-агентов, а также тем, кто ищет лучший редактор для решения своих задач. Введение В эпоху стремительного развития технологий, когда скорость вывода продуктов на рынок становится ключевым фактором успеха (TTM), традиционные методы разработки программного обеспечения сталкиваются с новыми вызовами. Одним из наиболее перспективных решений является использование low-code платформ — инструментов, позволяющих создавать приложения с минимальным количеством написания кода вручную. Особенно интересными становятся low-code редакторы, интегрированные с большими языковыми моделями (LLM),которые позволяют автоматизировать разработку и повысить эффективность работы разработчиков. Цель данной статьи — провести сравнительный анализ четырех популярных low-code редакторов: Flowise, LangFlow, n8n и Dify. Эти платформы предоставляют различные подходы к созданию приложений на основе LLM, каждая из которых имеет свои уникальные особенности и преимущества. 1. Описание приложений на основе LLM (основные виды, обзор рынка) Приложения на основе больших языковых моделей (LLM) представляют собой относительно новый класс программного обеспечения, которое способно решать множество задач благодаря использованию мощных алгоритмов машинного обучения. В контексте low-code редакторов, LLM играют ключевую роль в автоматизации процессов разработки, позволяя создавать функциональные приложения с минимальными затратами времени и усилий.
Long text about experimentation with some AI tools.
Datastax neemt start-up achter low-code ai-builder langflow over https://www.trendingtech.news/trending-news/2024/04/4915/datastax-neemt-start-up-achter-low-code-ai-builder-langflow-over #DataStax overname #Langflow AI-builder #Generatieve AI #NoSQL database #Low-code ontwikkeling #Trending #News #Nieuws